Trends H1 2025: Cyber Insights

Introduction
To protect our users, Quad9 blocks DNS lookups of malicious host names from an up-to-the-minute list of threats. This blocking action protects your computer, mobile device, or IoT systems against a wide range of threats such as malware, phishing, spyware, and botnets, and it can improve performance and privacy. This blogpost provides security insights on the threats blocked by Quad9 DNS between January and June 2025. The report combines DNS telemetry data and open-source intelligence with statistics and analysis to provide security insights on the top malicious domains visited by our users and blocked by Quad9 DNS. Additionally, the post presents key regional threats targeting Quad9 users.
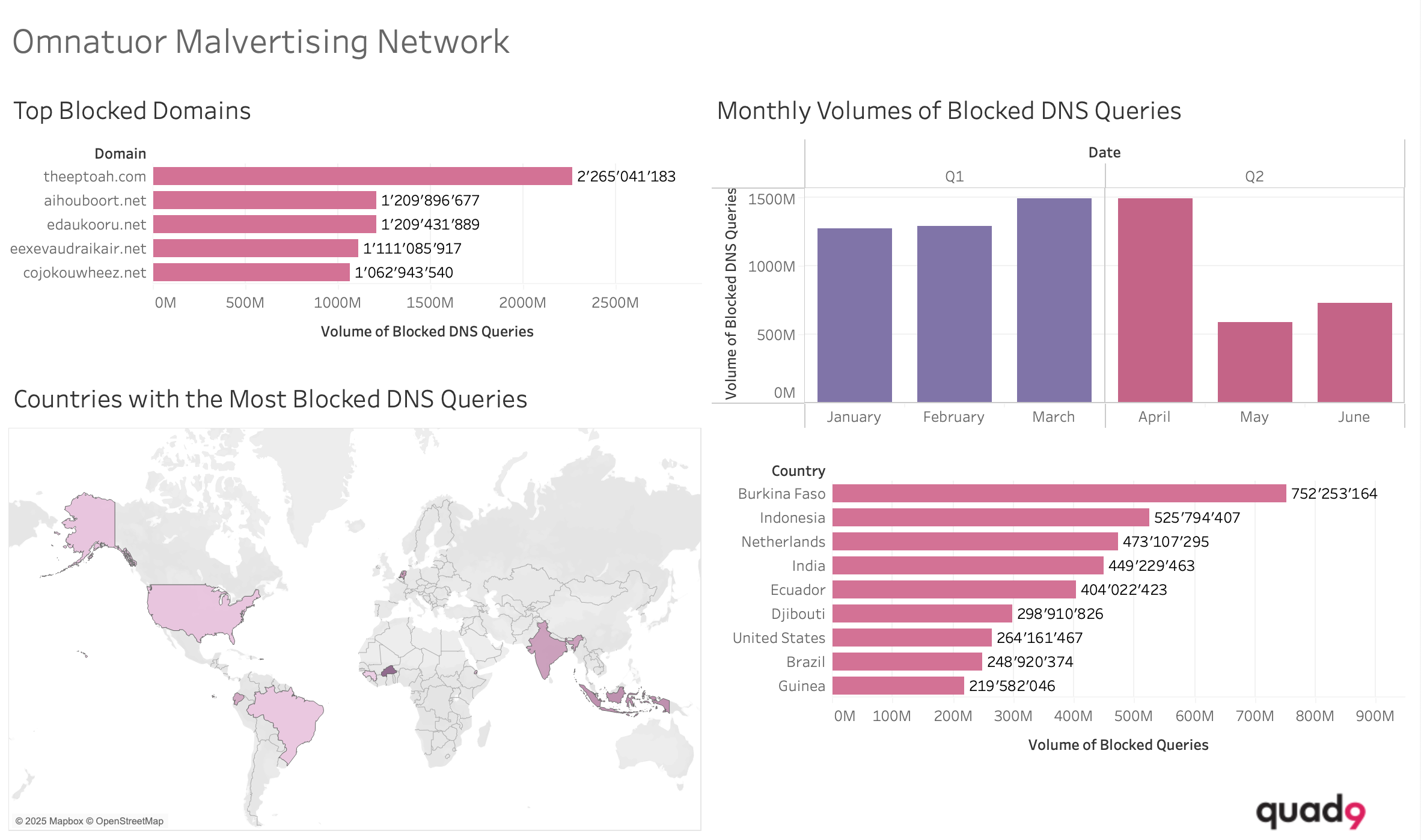
Omnatour Malvertising: A Persistent Top Threat
It should not come as a surprise that Omnatuor malvertising campaigns continue to plague users globally. Previously highlighted in our Cyber Insights reports, these attacks hijack browser settings to distribute harmful riskware. Cybercriminals exploit compromised websites to deliver spyware, employing sophisticated evasion techniques to avoid detection. In the first half of 2025, the Omnatour malvertising network proved to be an overwhelming force, accounting for the top 5 most blocked domains by Quad9. This resulted in an astounding 6.9 billion blocked queries attributed to just these five domains alone.
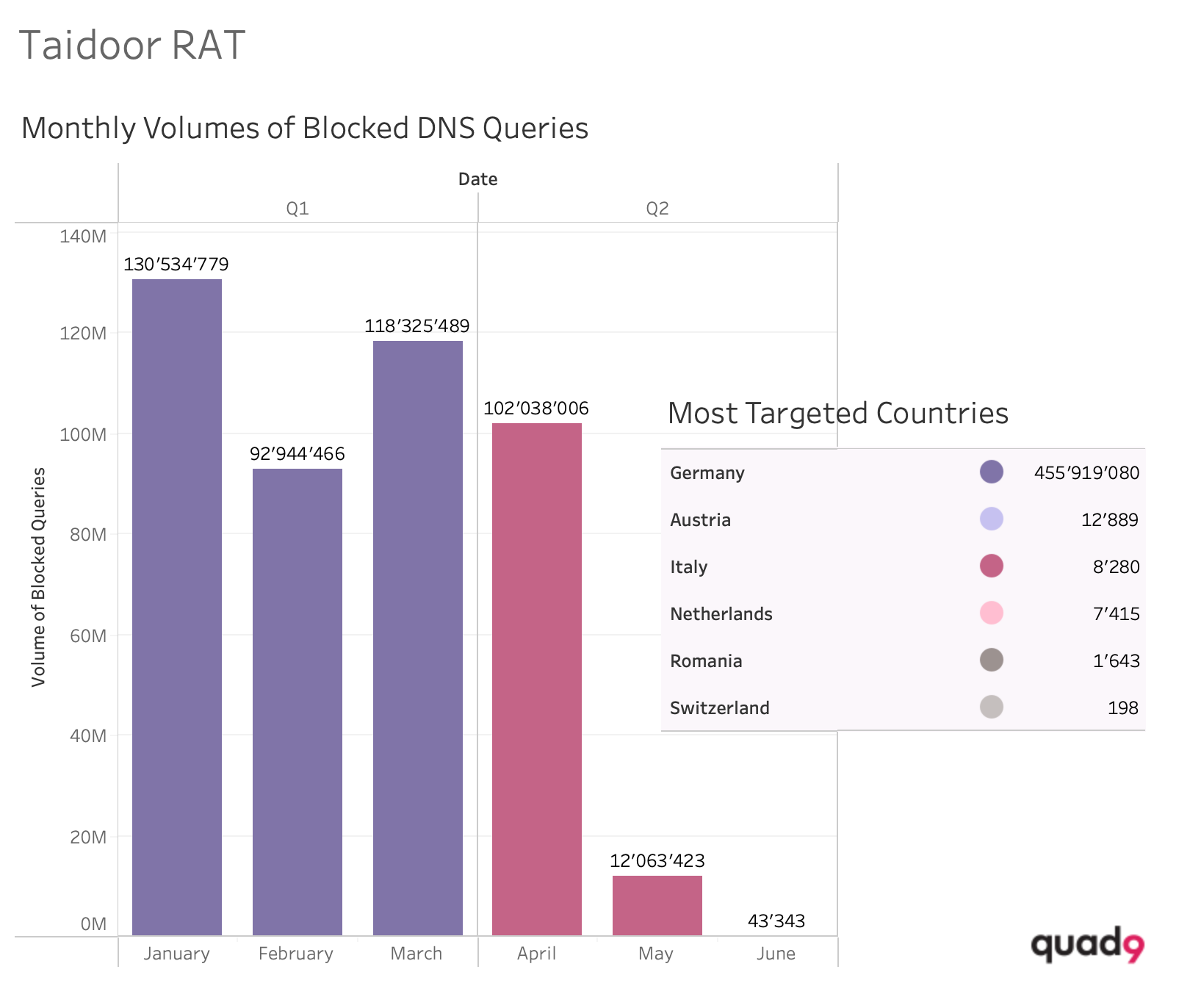
Taidoor RAT
The Taidoor Remote Access Trojan (RAT) is a sophisticated piece of malware used by Chinese government-backed cyber actors to maintain a persistent presence on victim networks and facilitate further exploitation. Once installed, Taidoor can perform a variety of malicious activities, including:
- Remote Control: It allows attackers to execute arbitrary commands and applications on the compromised system.
- Data Exfiltration: The RAT is capable of collecting and exfiltrating sensitive data and files from the victim’s machine.
- System Reconnaissance: It can gather system information, such as file system data, MAC addresses, network adapter details, and system time. It can also discover running processes and query the system registry.
- Persistence: Taidoor establishes persistence on the victim’s network, often by modifying registry keys, to ensure continued access even after a system reboot.
- File Operations: It can perform various file operations, including downloading and uploading files, and deleting files.
- Screenshot Capture: The malware has the ability to capture screenshots of the victim’s desktop.
- Foothold for Further Attacks: Taidoor is often used as an initial foothold, enabling attackers to conduct further reconnaissance, propagate within the network, and deliver additional malicious payloads.
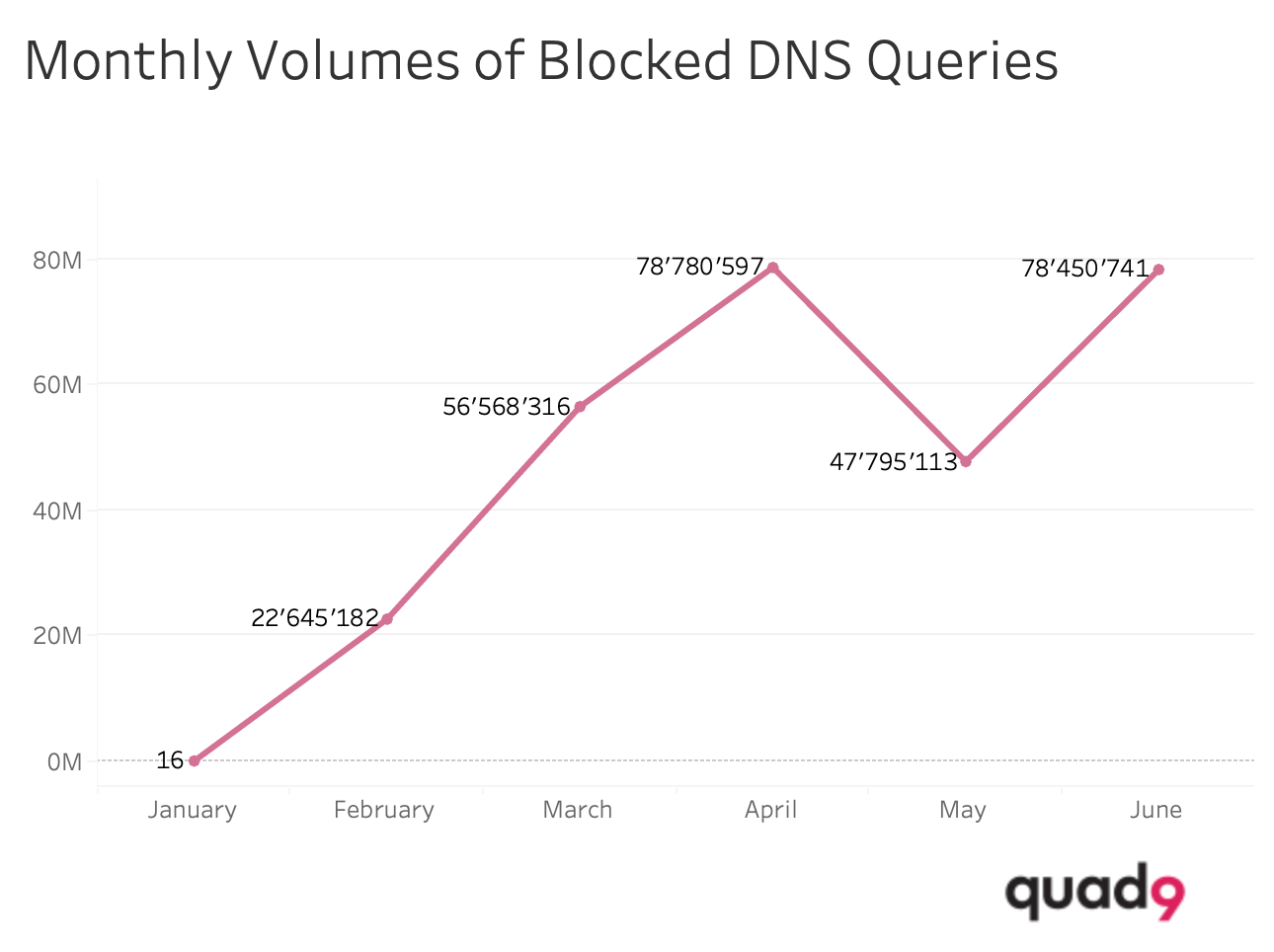
Phishing - Fake Taco Bell Gift Card Scam
The Fake Taco Bell Gift Card Scam predominantly leverages online tactics, where fraudsters impersonate the brand through deceptive social media posts, emails, or fake websites. These scams typically lure victims with promises of free gift cards or substantial monetary rewards, often contingent on providing personal information or making a small payment, frequently requested in the form of another gift card. In such scenarios, the promised gift card is never delivered, and the victim’s personal data or funds are stolen. It’s crucial for consumers to exercise caution, only engaging with official Taco Bell channels for promotions, and to be wary of any offer that seems overly generous or requires unusual payment methods.
As depicted on the graph below, we observed a growing number of blocked DNS queries to the domains attributed to the fake Taco Bell gift card scam:
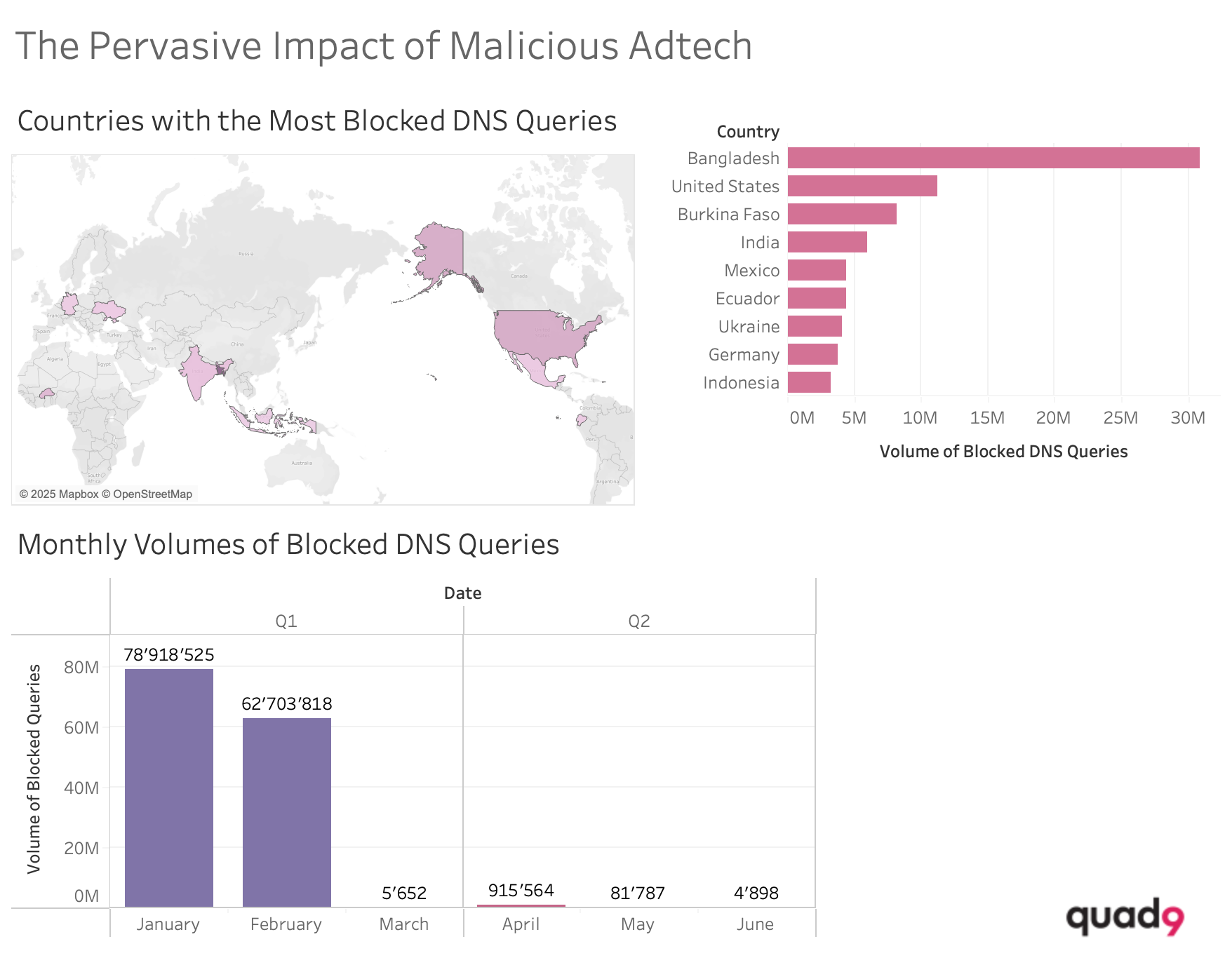
The Pervasive Impact of Malicious Adtech
Ever wonder just how deeply malicious ads can sink their hooks into your digital life? Infoblox’s own VP of Threat Intel, Renée Burton, decided to find out, diving down the rabbit hole of a compromised website. The study involved visiting a hacked domain that initiated a series of redirects through traffic distribution systems (TDSs), culminating in the acceptance of push notifications. Subsequently, the test device received in excess of 100 malicious notifications daily, propagating various scams, deceptive applications, and malware. The research revealed a sophisticated ecosystem of adtech entities that not only facilitate but actively profit from these compromised domains. Furthermore, the findings underscore the significant challenge users face in mitigating exposure to manipulated content, even after standard browser data clearance procedures. The report ultimately posits that these adtech organizations frequently function as active enablers of cybercrime, particularly through scareware tactics.
At Quad9, in the first six months of 2025, we blocked more than 142 million DNS queries to the domain attributed to the TDS used in the campaign.
Conclusions
Over the years, it’s become easier and cheaper for cybercriminals to attack Internet users. Quad9’s mission is to improve the security and stability of the Internet and reduce users’ vulnerability to risk and become more effective in their daily online interactions - even in the face of growing cyber attacks.
By preventing connections to known malicious sites, Quad9 reduces exposure to risks before they are downloaded to computers or a victim can see the fraudulent website. The inability to reach a malicious host means that defenses such as virus protection or user-based detection such as certificate examination are never called into action.
As a DNS provider, Quad9 has the unique opportunity to analyze the volumes and trends of malware campaigns. If you are a security researcher or threat intelligence provider and want to hear more, contact us via our website at: https://quad9.net/support/contact
About Quad9
Quad9, a nonprofit in the US and Switzerland, provides free cybersecurity services to the emerging world via secure and private DNS lookup. Quad9 operates in over 245 locations across more than 110 nations, blocking hundreds of millions of malware, phishing, and spyware events daily for millions of end users. Quad9 reduces harm in vulnerable regions, increases privacy against criminal or institutionalized interception of Internet data, and improves performance in under-served areas.
