Trends H2 2025: Cyber Insights

Introduction
To protect our users, Quad9 blocks DNS lookups of malicious host names from an up-to-the-minute list of threats. This blocking action protects your computer, mobile device, or Internet of Things (IoT) systems against a wide range of threats, such as malware, phishing, spyware, and botnets, and it can improve performance and privacy. This blogpost provides security insights on the threats blocked by Quad9 DNS between July and December 2025. This time we analyzed the top 25 domains blocked by us. The report combines DNS telemetry data and open-source intelligence with statistics and analysis to provide security insights on the top malicious domains visited by our users and blocked by Quad9 DNS.
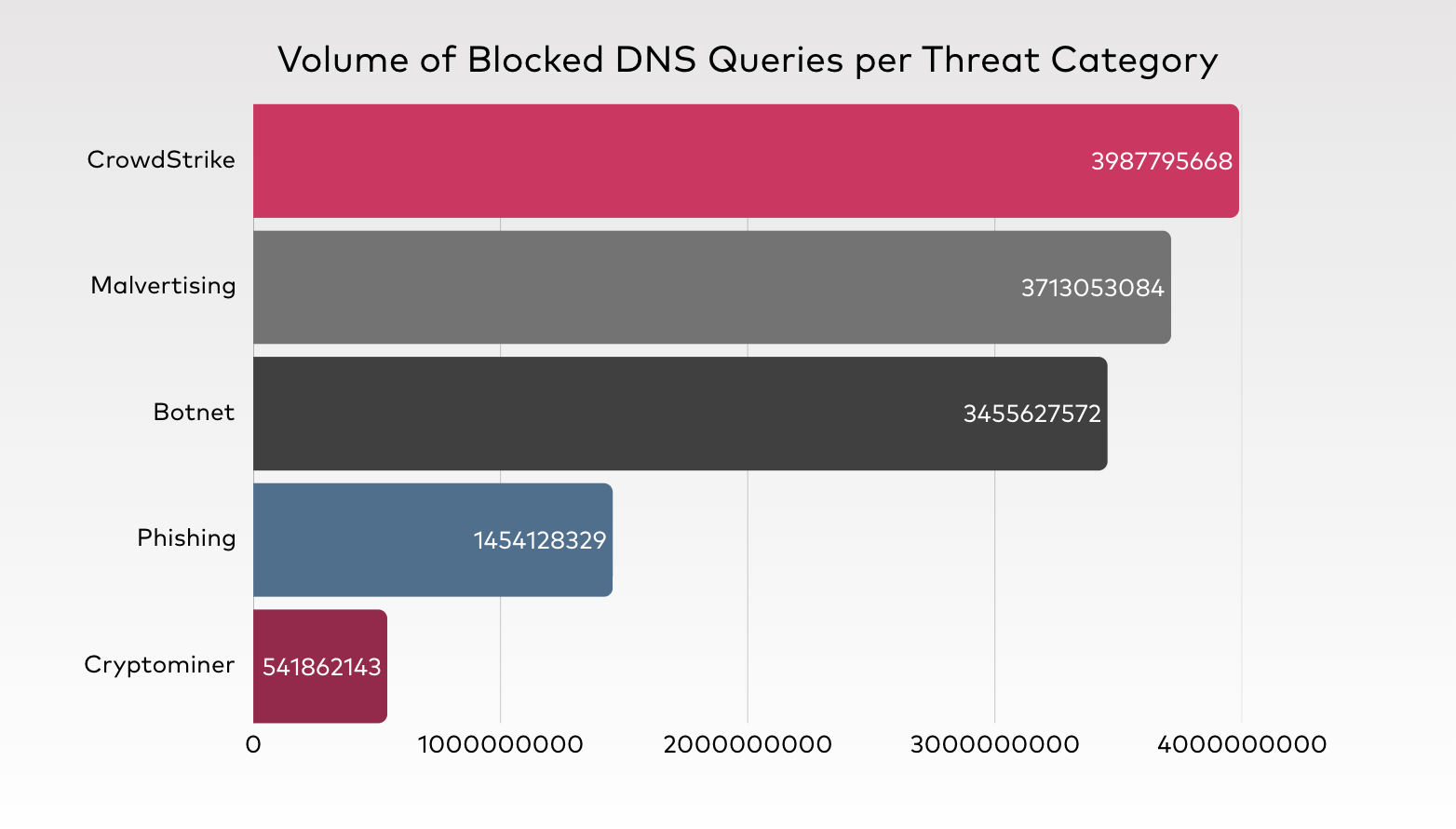
To better understand the nature of the high-volume threats targeting our Quad9 users, we categorized the top 25 blocked domains by their primary intent. The following chart illustrates the distribution of these threats, revealing a significant concentration in CrowdStrike mimicking domains in relation to the CrowdStrike outage in 2024 and malvertising infrastructures.
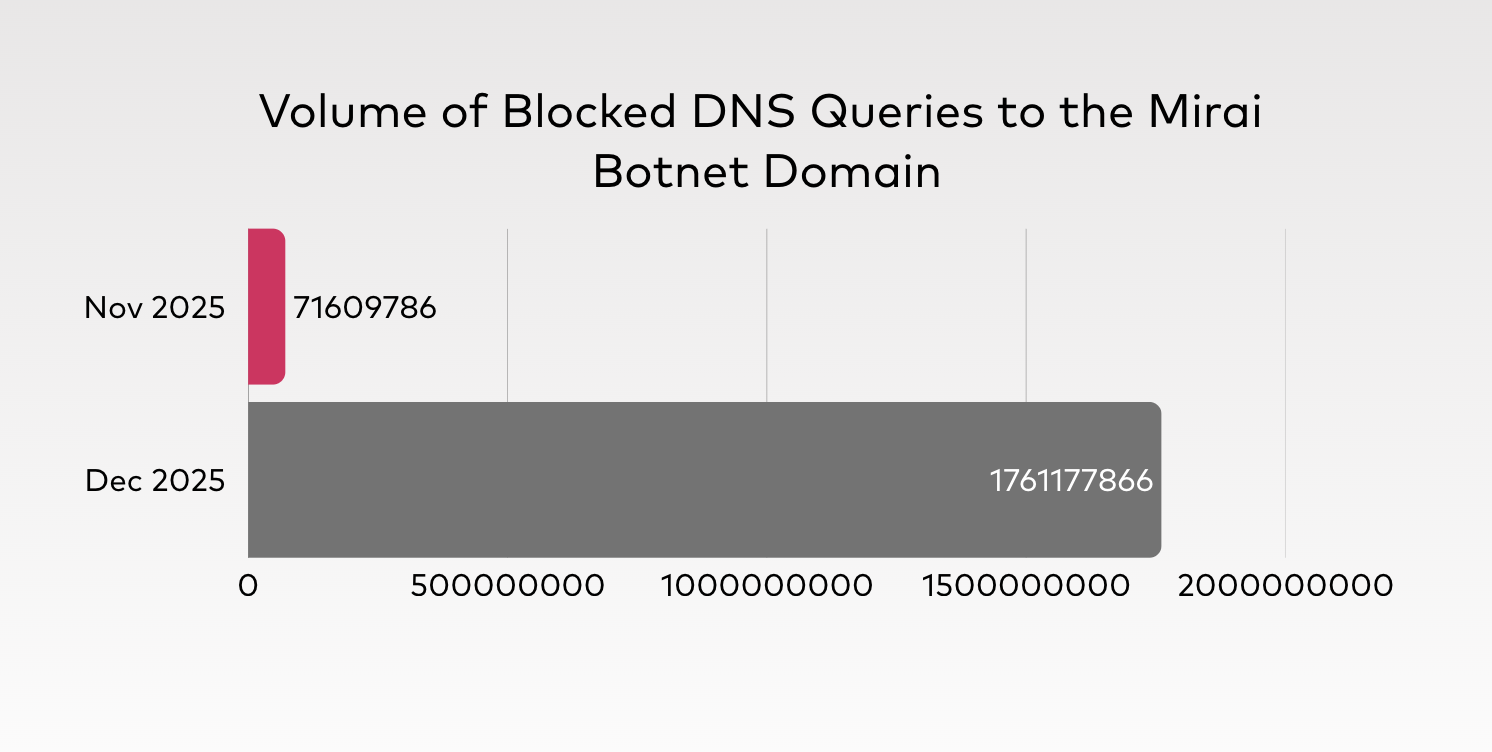
Mirai Botnet: 1.8 Billion Monthly Queries to a Single Domain
The Mirai botnet remains one of the most persistent and evolving threats in the cybersecurity landscape since its source code was famously leaked in 2016. Originally designed to enslave insecure IoT devices - such as IP cameras, DVRs, and home routers - by exploiting weak factory-default credentials, Mirai has since spawned numerous variants that continue to plague modern networks. The scale of its operations is often staggering; for instance, our analysis of top blocked domains revealed a single domain attributed to the Mirai botnet (perferctdmng[.]is) received more than 1.8 billion queries in just one month.
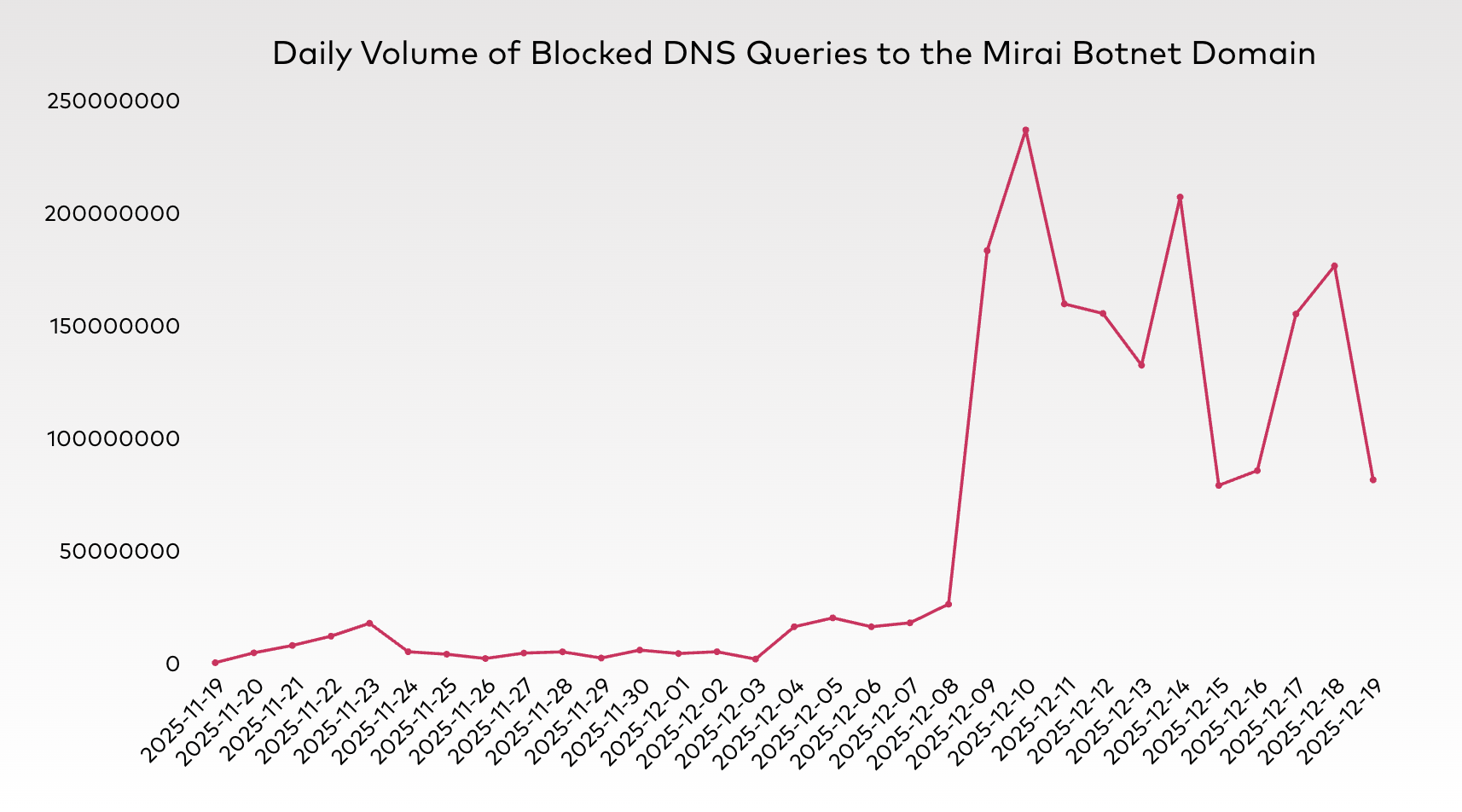
This massive volume of traffic highlights the nature of Mirai’s automated scanning and Command & Control (C2) communications, where hundreds of thousands of infected “zombie” devices continuously attempt to “phone home” or receive instructions for large-scale Distributed Denial of Service (DDoS) attacks.
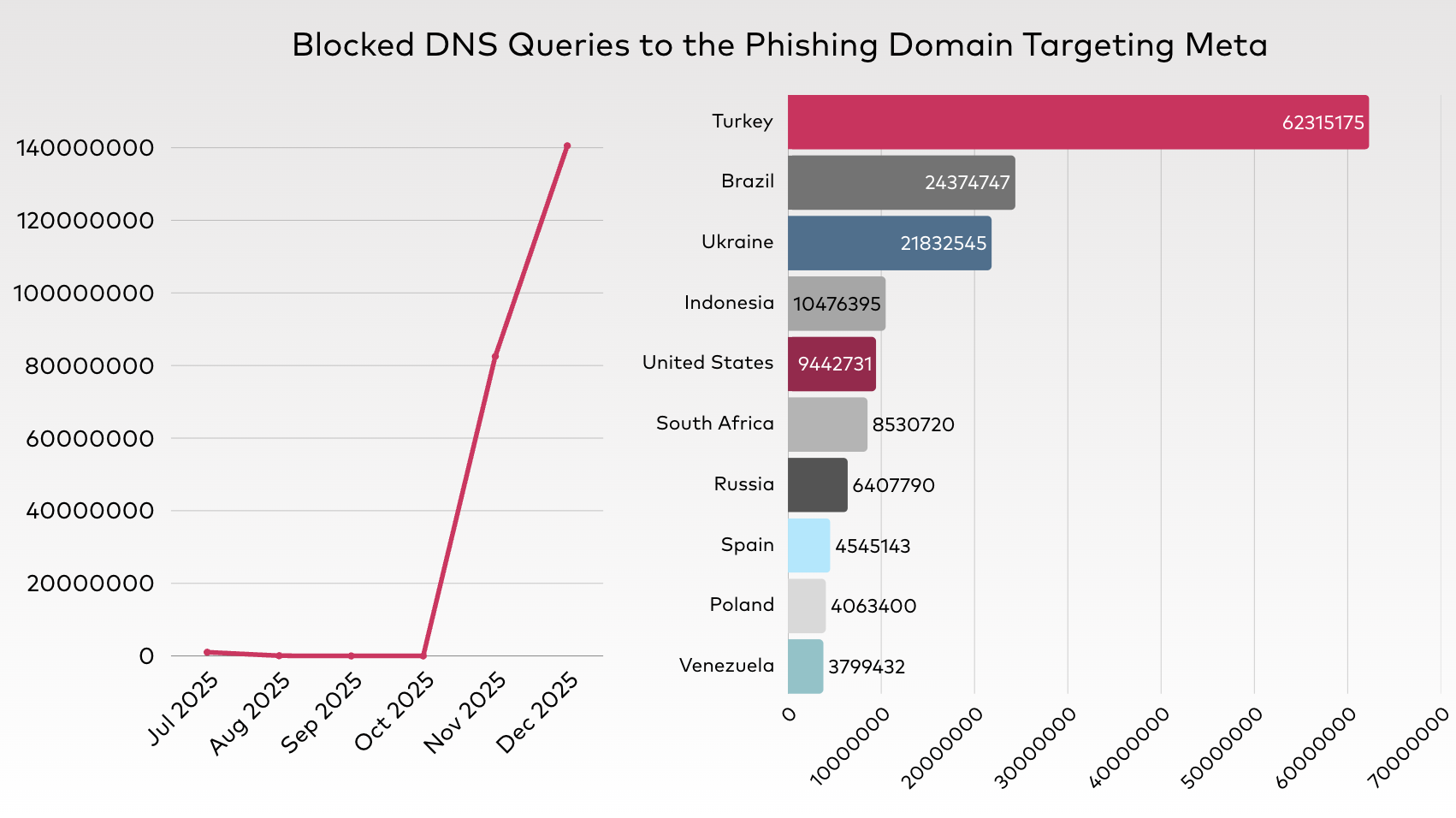
Impersonation Risks: Analyzing 224M Queries to Fake Meta Support Domains
Beyond high-volume botnet activity, we also identified significant traffic directed toward metaverifiedsupport[.]net, a domain that masquerades as an official support channel for Meta Verified services. In H2 2025, we blocked 224,128,635 queries to this domain, with the highest concentration of activity originating from users in Turkey and Brazil. Our analysis confirms that this is a fraudulent domain used primarily for email forwarding in phishing and spam campaigns. The use of a “.net” TLD is a common red flag for credential harvesting operations designed to exploit users seeking account verification or assistance.
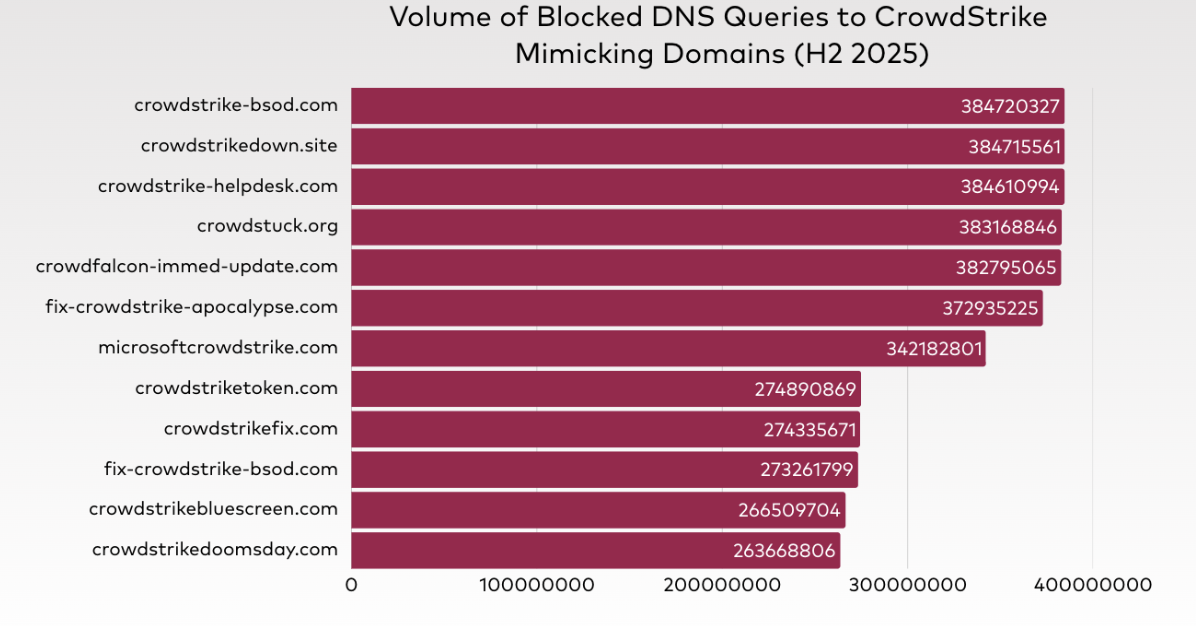
Threat Actors Exploiting CrowdStrike Incident
In July 2024, a faulty update to CrowdStrike’s Falcon Sensor security software caused widespread disruption across global IT systems. This incident resulted in millions of Windows computers crashing, severely impacting critical services in various sectors including air travel, banking, and healthcare. After the incident, CrowdStrike Intelligence has observed threat actors exploiting the Falcon Sensor incident. These actors are engaging in various malicious activities including:
- Phishing emails: Disguised as legitimate support communications from CrowdStrike.
- Impersonation: Posing as CrowdStrike staff during phone calls.
- False research claims: Presenting themselves as independent researchers, falsely linking the technical issue to a cyberattack and offering remediation guidance.
- Malicious scripts: Selling scripts that allegedly automate recovery from the content update issue, likely containing malicious code.
Quad9 blocked domains abused by those Threat Actors. In total, in H2 2025, we observed more than 3.9 billion DNS queries to 12 domains.
Omnatour Malvertising: A Persistent Top Threat
It should not come as a surprise that Omnatuor malvertising campaigns continue to plague users globally. Previously highlighted in our Cyber Insights reports (H1 2025, H2 2024, H1 2024), these attacks hijack browser settings to distribute harmful riskware. Cybercriminals exploit compromised websites to deliver spyware, employing sophisticated evasion techniques to avoid detection. In the second half of 2025, the Omnatour malvertising network proved to be an overwhelming force, accounting for the top 5 most blocked domains by Quad9. This resulted in an astounding 3.7 billion blocked queries attributed to just these four domains alone.
Conclusions
Over the years, it’s become easier and cheaper for cybercriminals to attack Internet users. Quad9’s mission is to improve the security and stability of the Internet, reducing users’ vulnerability to risk and helping them become more effective in their daily online interactions - even in the face of growing cyber attacks.
By preventing connections to malicious sites, Quad9 eliminates exposure to risks before they are downloaded to computers or a victim can access the fraudulent website. The inability to reach a malicious host means that defenses, such as virus protection, or user-based detection, such as certificate examination, are never called into action.
As a DNS provider, Quad9 has the unique opportunity to analyze the volumes and trends of malware campaigns. If you are a security researcher or threat intelligence provider and want to hear more, contact us via our website at: https://quad9.net/support/contact
About Quad9
Quad9 is a global nonprofit DNS security service that protects users from phishing, malware, botnets and other malicious domains by blocking threats at the DNS layer. Based in Switzerland and operating under strict privacy laws, Quad9 serves more than 100 million users worldwide, including public institutions, enterprises, ISPs, and individuals seeking free, privacy-first cyber protection.
References:
https://www.reversinglabs.com/blog/taidoor-a-truly-persistent-threat
https://blogs.infoblox.com/threat-intelligence/pushed-down-the-rabbit-hole/
